Social media, as the documentary The Social Dilemma explains, is an addictive force that has nearly everyone (in the developed world) addicted. This is not new this year, but rather has been an ongoing and increasingly acute phenomenon. Today, no one would blame you if you avoided logging on to Facebook or Twitter for fear of a barrage of political posts and advertisements. It wasn’t always this way. The political takeover of social media wasn’t an accident.
In the United States, social media’s influence in politics first emerged as a force to be reckoned with in 2008, during the United States presidential election. According to Dr. Pamela Rutledge, a self-described ‘media psychologist’, Barack Obama’s win was in part explained by his campaign’s savvy use of technology, including the internet and social media (Rutledge, 2013). For example, Barack Obama had over 2 million Facebook likes, while John McCain (his opponent in 2008) had only about 600,000 (2008 United States presidential election, 2020). If the Facebook likes were votes, that would have given Obama over 75% of the vote. In reality, he won with about 53% of the vote. There are obviously other explanations for the online popularity disparity, such as an over-representation of younger people online (at the time).
In 2012, Obama again beat back his opponent with the aid of a sophisticated (for the time) social media campaign. Rutledge attributes this second win to several factors. Obama’s 2012 campaign hired a larger social media team than in 2012, but this makes sense. Social media use had doubled from about 37% (of American adults) in 2008 to 69% in 2012. Obama also had a head-start, a holdover from the extensive networks built during his prior run. However, Rutledge alleges that the real reason Obama’s social media presence was so successful is because his campaign understood how social networks operate. In this case, the term refers to human social behavior instead of social media companies. In short, the Obama campaign’s online presence was successful because they created better memes that spread farther than the competition (Rutledge, 2013).
The final reason that Obama won the internet game in 2012 was that his campaign made use of big data. They were able to predict which voters were persuadable and what message would be effective for different groups of voters (Rutledge, 2013). Does this sound familiar? It should, since this is the same strategy that was (in)famously used by Cambridge Analytica in 2016’s presidential election.
The Cambridge Analytica scandal involved a private political consulting firm (Cambridge Analytica) which obtained access to user data from Facebook and used that data to build profiles on voters and target ads and other messages at them to influence their voting behavior. It’s possible that the Cambridge Analytica scandal blew up the way it did because it received a larger share of ‘blame’ for the way the 2016 election turned out than it deserved. However, the scandal had a huge impact on people’s trust in social media companies and began an awakening where people began to think more about the information that was collected while they navigated the internet and social media. Certainly, Facebook itself faced a large backlash as a result and subsequently engaged in a multi-year PR campaign to try and salvage their reputation (Wong, 2019).
Most people are aware that social media companies use information that they collect about you to serve up ads. People are divided on whether there is any harm here or whether that is a fair trade for the service provided. Fewer people are aware of the intentionally addictive nature of social media or how it also engages in behavior modification, rather than simply driving engagement or serving targeted ads (Orlowski, 2020). People are increasingly producing and sharing political content on social media platforms, and all of that activity generates data that can be used to predict the political views of those users. How does data collection interact with digital activism?
In the United States, most people would probably assume that data collection and maybe a few lost online followers were the worst things they had to fear from sharing their political views online. That’s not necessarily the case. As Chris Brooks from the online newspaper The Intercept reports: The FBI has been investigating and harassing Black Lives Matter organizers. After creating Facebook events for Black Lives Matter rallies, several activists in Tennessee were questioned by the FBI about Antifa (Brooks, 2020). In fact, this is part of a larger pattern of FBI behavior of monitoring and suppressing black political movements, going back to the Civil Rights movement of the 1960’s (Speri, 2019).
Intimidation of political dissidents is not a new thing, and of course it isn’t limited to the United States. In Saudi Arabia, Twitter is a popular way for activists to anonymously raise awareness of their issues in a country where freedom of speech is not guaranteed. Despite this, the Women2Drive movement eventually resulted in women being given the right to drive in Saudi Arabia. Twitter was an important tool to help make this happen, because it provides an anonymous persona from which to speak publicly. However, it’s also a dangerous one. In 2017, some activists heard rumors of a coming crackdown on political dissent. They deleted their tweets as a preventative measure. However, Twitter makes an archive of past tweets (even deleted ones) available to data miners (including governments) who wish to aggregate data about tweets. This data can be used to de-anonymize the tweets and prosecute activists. In Saudi Arabia, women were being arrested and detained for activism almost up until the government changed its position (Al-Sharif, 2018).
Some activism can be more dramatic than organizing a march or asking to be able to drive a car, though. The Arab Spring was largely fueled by social media, Twitter in particular. That movement resulted months-long protests in multiple countries throughout the Middle-East region. Countries with Arab Spring uprisings included Egypt, Libya, Syria, Yemen, and others. In Egypt, the government was eventually overthrown once the military sided with protesters. In Syria and Libya, civil war resulted after the government refused to step down. Further, the rise of ISIS/ISIL can be traced to the Arab Spring (Arab Spring, 2020). ISIS was well-known for using social media for recruitment. They had a sophisticated social media content generation machine that ran accounts on social media networks such as Facebook, Twitter, Telegram, and more recently TikTok, among others (until those accounts were shut down). This sophisticated social media presence is credited with enabling their rapid growth and emergence as an existential threat to several Middle-Eastern nations simultaneously, as well as their ability to reach across the globe and inspire terrorist acts in far-away countries such as the United States, France, Germany, and Russia (Use of social media by the Islamic State of Iraq and the Levant, 2020).
Islamic extremism is hardly the only form of extremism that social media intensifies and helps to propagate. In the United States, there has long been a militia movement among (primarily) right-wing groups. Beginning during the Obama presidency (2009-2017) and continuing through this day, the militia movement has grown. Today, there are more than twice as many militia groups as there were in 2009 (Why armed militia groups are surging across the nation, 2017). More recently, these groups have become more organized. One network of militias is called the 3 percenters (the name is a reference to the number of colonists who took up arms against the king). This group recruits in part through a social network called Zello and also maintains ties to local police and military members (Loewinger, 2020). These militias have been present numerous events between 2013 and 2020, including the Unite the Right rally in 2017 as well as several BLM rallies this year. A separate militia group calling themselves the Wolverine Watchmen was arrested this year before they were able to pull off a scheme to abduct the governor of Michigan. The scheme was apparently intended to instigate a civil war, according to CBS News (Quinn, 2020).
Violent extremism, whether political or religious is indefensible. Those who are drawn in to such organizations would surely be better served by a psychiatric professional. However, the harm they can do is real. Is it good that the FBI foiled a terrorist attack on a sitting US governor? Is it bad that the FBI stopped a BLM rally? Yes. In the United States, nonviolent political speech, such as a rally, is protected from government action. Violent acts motivated by political reasons (the definition of terrorism) are not.
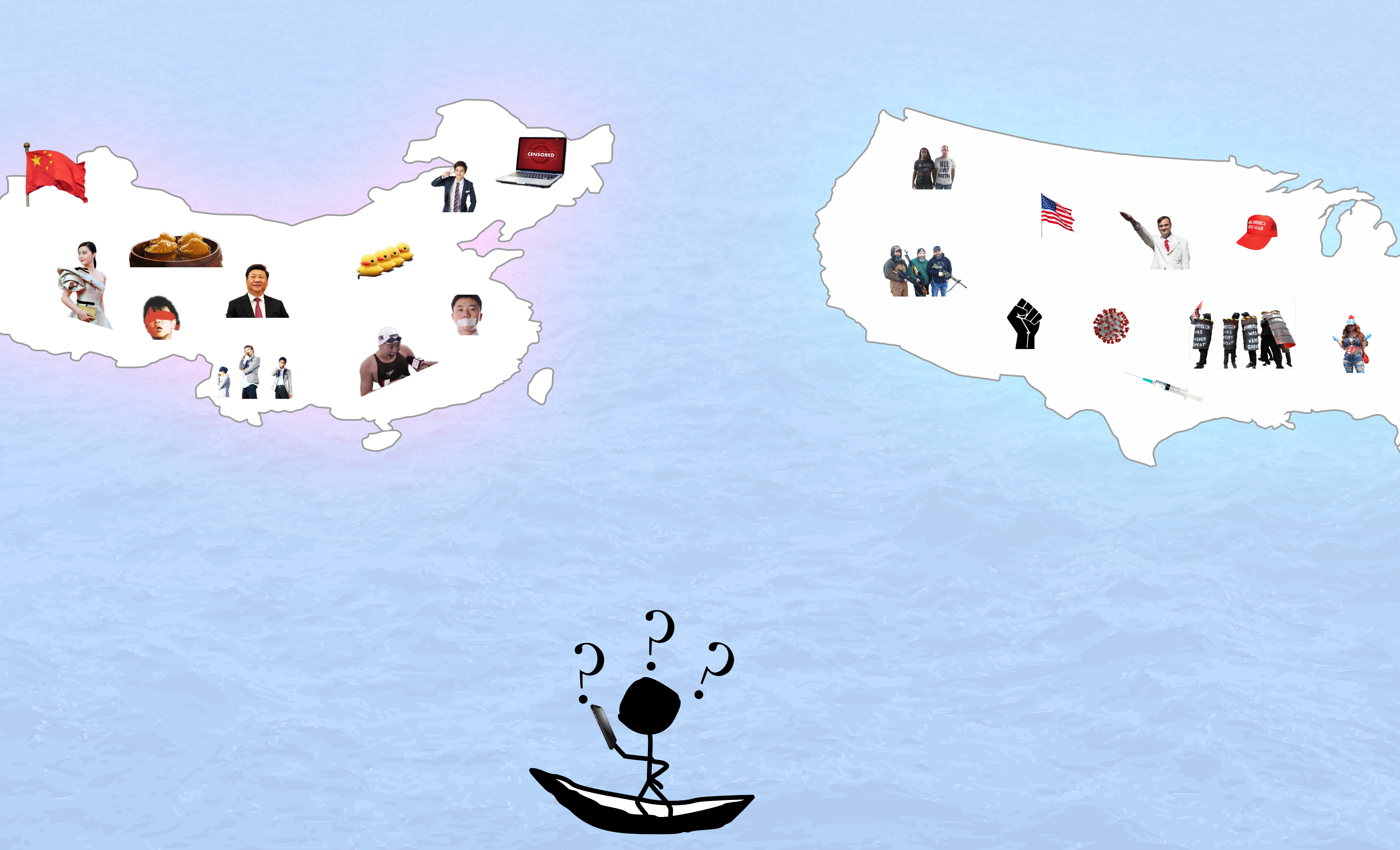
In the United States, we (theoretically) enjoy protected free speech, including political speech. However, as mentioned above in reference to Saudi Arabia, that is not the case everywhere in the world. A particularly advanced threat to free political speech is China. In China, news outlets, social media platforms, and individuals (such as bloggers and vloggers) must all conform to censorship guidelines set by the Party leadership. Failure to comply can result in police harassment, deletion of your online presence, or arrest (Hernández, 2019). Internet companies that operate under this censorship regime have learned that they must play by the rules or face harsh penalties themselves. Twitter, Google, and Facebook are banned in China in part because they did not agree to the censorship and data sharing requirements in place. Social media platforms that host offending content or refuse to share individual user data, they risk being ordered to shutter their business with little notice or even jail time for the company executives (Zhong, 2018), (Mozur, 2020).
The Censorship rules in China are somewhat vague. Sometimes it is clear what violation prompted the state censors to take action, and other times it’s not. Worse, violators often aren’t aware that they’ve trespassed until after action is taken against them. This has resulted in corporations being very proactive in regulating their own platforms. Likewise, individuals often avoid discussing or seeking out information on sensitive topics. Chinese online platforms, like other internet platforms based in the United States, have found content moderation to be essential to their business. Also, like American internet companies, they often subcontract this work out to firms that specialize in content moderation. However, unlike American firms, the scope of content moderation is much broader. American based online platforms moderate pornography and violent content to varying degrees, and increasingly moderate political misinformation to a lesser degree. However, in China this content moderation is not optional. Failure to properly moderate a platform to the Party’s satisfaction can result in the sanctions mentioned earlier (Internet censorship in China, 2020).
In the United States, a law known as Section 230 provides online platforms with immunity from liability for the content that users of those same platforms produce. It is often cited as being necessary to protect freedom of expression on the internet (In the United States), and as the basis for all online platforms in the US. However, China has online platforms without an equivalent to Section 230. China surely doesn’t have freedom of expression, but they also have largely avoided the politicization of the internet that has occurred here, and they have avoided much of the extremism found in other parts of the world as that kind of content is removed by censors before it can spread and proliferate. This censorship regime has been so successful that many young Chinese have never heard of the Tiananmen Square incident. In fact, according to the New York Times, many people no longer have a desire to seek out censored content (Yuan, A Generation Grows Up in China Without Google, Facebook or Twitter, 2018). It is impossible to search for something you don’t know exists. In fact, the success of the censorship has made it difficult to hire new content moderators (censors). Another New York Times article revealed that new-hires at one content moderation company must go through training that teaches them, among other things, what Tiananmen square was and what code words people use to reference it (Yuan, Learning China’s Forbidden History, So They Can Censor It, 2019).
A censorship model such as the Chinese government uses is not right for the United States, where political expression is expected to be free from government interference. However, it is clear that it is possible to curb the spread of extremism through online platforms. China has demonstrated it. They have also demonstrated that Section 230 is not necessary for the survival of online platforms, as those also exist in China, where platforms are liable for content that users produce. What kind of changes can the United States make to prevent stifling of political expression, while also combating disinformation and extremism? Perhaps we should not go so far as China has, but maybe we can learn from their example and find a way to adapt some of their model to fit our differences.
References
2008 United States presidential election. (2020, October 26). Retrieved from Wikipedia: https://en.wikipedia.org/wiki/2008_United_States_presidential_election#Internet_campaigns
Al-Sharif, M. (2018, 9 16). The Dangers of Digital Activism. Retrieved from The New York Times: https://www.nytimes.com/2018/09/16/opinion/politics/the-dangers-of-digital-activism.html
Arab Spring. (2020, 10 26). Retrieved from Wikipedia: https://en.wikipedia.org/wiki/Arab_Spring#Summary_of_conflicts_by_country
Brooks, C. (2020, 6 12). After Barr Ordered FBI to “Identify Criminal Organizers,” Activists Were Intimidated at Home and at Work. Retrieved from The Intercept: https://theintercept.com/2020/06/12/fbi-jttf-protests-activists-cookeville-tennessee/
Hernández, J. C. (2019, 3 16). Why China Silenced a Clickbait Queen in Its Battle for Information Control. Retrieved from The New York Times: https://www.nytimes.com/2019/03/16/world/asia/china-bloggers-internet.html
Internet censorship in China. (2020, 10 28). Retrieved from Wikipedia: https://en.wikipedia.org/wiki/Internet_censorship_in_China
Loewinger, M. (2020, 10 16). Emergency Mode. Retrieved from On the Media: https://www.wnycstudios.org/podcasts/otm/episodes/on-the-media-emergency-mode
Mozur, P. (2020, 7 7). In Hong Kong, a Proxy Battle Over Internet Freedom Begins. Retrieved from The New York Times: https://www.nytimes.com/2020/07/07/business/hong-kong-security-law-tech.html
Orlowski, J. (Director). (2020). The Social Dilemma [Motion Picture].
Quinn, M. (2020, 10 9). Feds bust alleged plot to kidnap Michigan Governor Gretchen Whitmer. Retrieved from CBS News: https://www.cbsnews.com/news/gretchen-whitmer-michigan-governor-fbi-kidnapping-plot/
Rutledge, P. (2013, 01 13). How Obama Won the Social Media Battle in the 2012 Presidential Campaign. Retrieved from DR. Pamela Rutledge: https://www.pamelarutledge.com/2013/01/25/how-obama-won-the-social-media-battle-in-the-2012-presidential-campaign/
Speri, A. (2019, 10 29). The FBI Spends a Lot of Time Spying on Black Americans. Retrieved from The Intercept: https://theintercept.com/2019/10/29/fbi-surveillance-black-activists/
Use of social media by the Islamic State of Iraq and the Levant. (2020, 10 26). Retrieved from Wikipedia: https://en.wikipedia.org/wiki/Use_of_social_media_by_the_Islamic_State_of_Iraq_and_the_Levant
Why armed militia groups are surging across the nation. (2017, 4 19). Retrieved from PBS Newshour: https://www.pbs.org/newshour/show/armed-militia-groups-surging-across-nation
Wong, J. C. (2019, 3 18). The Cambridge Analytica scandal changed the world – but it didn’t change Facebook. Retrieved from The Guardian: https://www.theguardian.com/technology/2019/mar/17/the-cambridge-analytica-scandal-changed-the-world-but-it-didnt-change-facebook
Yuan, L. (2018, 8 6). A Generation Grows Up in China Without Google, Facebook or Twitter. Retrieved from The New York Times: https://www.nytimes.com/2018/08/06/technology/china-generation-blocked-internet.html
Yuan, L. (2019, 1 2). Learning China’s Forbidden History, So They Can Censor It. Retrieved from The New York Times: https://www.nytimes.com/2019/01/02/business/china-internet-censor.html
Zhong, R. (2018, 4 11). It Built an Empire of GIFs, Buzzy News and Jokes. China Isn’t Amused. Retrieved from The New York Times: https://www.nytimes.com/2018/04/11/technology/china-toutiao-bytedance-censor.html